DFARS 252.204-7012 - Safeguarding of Unclassified Controlled Technical Information
Prescribed in DFAR 204.7304 | |
| Effective Date: | 18 November 2013 |
| Clause or Provision: | Clause |
| Provision or Clause Number: | S 252.204-7012 - Safeguarding of Unclassified Controlled Technical Information |
| Principle Type And/Or Purpose of Contract: | |
| Required: | |
| Applicable: | |
| Optional: | |
| Subject: | |
| ProcurementType: | |
| Contract Threshold: | |
| Prescription Overview: |
Prescription OverviewUse the clause at 252.204-7012, Safeguarding of Unclassified Controlled Technical Information, in all solicitations and contracts, including solicitations and contracts using FAR part 12 procedures for the acquisition of commercial items. |
| Clause Overview: |
Clause Overview(a) Definitions. As used in this clause—(b) Safeguarding requirements and procedures for unclassified controlled technical informationThe Contractor shall provide adequate security to safeguard unclassified controlled technical information from compromise. To provide adequate security, the Contractor shall—
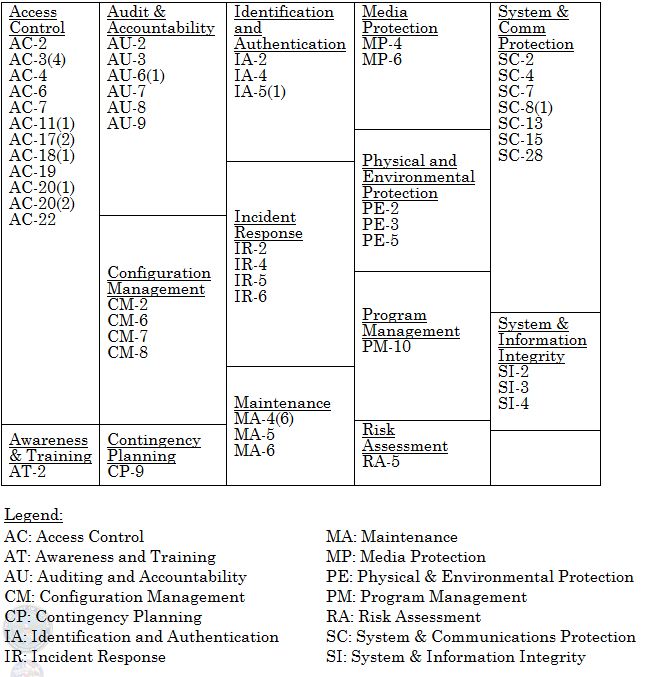
Table 1 -- Minimum Security Controls for SafeguardingMinimum required security controls for unclassified controlled technical information requiring safeguarding in accordance with paragraph (d) of this clause. (A description of the security controls is in the NIST SP 800-53, “Security and Privacy Controls for Federal Information Systems and Organizations” (http://csrc.nist.gov/publications/PubsSPs.html).) http://csrc.nist.gov/publications/nistpubs/800-53A-rev1/sp800-53A-rev1-final.pdf
(c) Other RequirementsThis clause does not relieve the Contractor of the requirements specified by applicable statutes or other Federal and DoD safeguarding requirements for Controlled Unclassified Information (CUI) as established by Executive Order 13556, as well as regulations and guidance established pursuant thereto. (d) Cyber Incident and Compromise Reporting(1) Reporting RequirementThe Contractor shall report as much of the following information as can be obtained to the Department of Defense via (http://dibnet.dod.mil/) within 72 hours of discovery of any cyber incident, as described in paragraph (d)(2) of this clause, that affects unclassified controlled technical information resident on or transiting through the Contractor’s unclassified information systems:
(2) Reportable Cyber IncidentsReportable cyber incidents include the following:
(4) Contractor actions to support DoD damage assessment. In response to the reported cyber incident, the Contractor shall—
(5) DoD damage assessment activities. If DoD elects to conduct a damage assessment, the Contracting Officer will request that the Contractor point of contact identified in the incident report at (d)(1) of this clause provide all of the damage assessment information gathered in accordance with paragraph (d)(4) of this clause. The Contractor shall comply with damage assessment information requests. The requirement to share files and images exists unless there are legal restrictions that limit a company's ability to share digital media. The Contractor shall inform the Contracting Officer of the source, nature, and prescription of such limitations and the authority responsible. (e) Protection of Reported InformationExcept to the extent that such information is lawfully publicly available without restrictions, the Government will protect information reported or otherwise provided to DoD under this clause in accordance with applicable statutes, regulations, and policies. The Contractor shall identify and mark attribution information reported or otherwise provided to the DoD. The Government may use information, including attribution information and disclose it only to authorized persons for purposes and activities consistent with this clause. (f) Law EnforcementNothing in this clause limits the Government’s ability to conduct law enforcement or counterintelligence activities, or other lawful activities in the interest of homeland security and national security. The results of the activities described in this clause may be used to support an investigation and prosecution of any person or entity, including those attempting to infiltrate or compromise information on a contractor information system in violation of any statute. (g) SubcontractsThe Contractor shall include the substance of this clause, including this paragraph (g), in all subcontracts, including subcontracts for commercial items. |
| Important Notes/Requirements: |
BackgroundEffective November 18, 2013 the Rule for Defense Federal Acquisition Regulation Supplement: Safeguarding Unclassified Controlled Technical Information was published for inclusion into DoD contracts and Prime subcontracts[1]. With the new rule there are:
DFARS CASE2011-D039 Additional Information/ResourcesReferences |
| Subcontract Threshold: | |
| Incorporated by Reference: | Yes |
| Uniform Contract Format: | |
| Editor: | Marshall |
Personal notes.